
Hardshell Cybersecurity Services
Hardshell offers a comprehensive suite of cybersecurity services designed to strengthen systems, networks, and data against digital threats, unauthorized access, and potential data breaches. Our expert team and cutting-edge technologies provide a range of specialized cybersecurity services to meet the diverse needs of our clients.
Zero Trust Architecture (ZTA)
Hardshell's strategic adoption of both Zero Trust Architecture (ZTA) and the National Institute of Standards and Technology (NIST) Cybersecurity Framework highlights its commitment to a thoughtful and forward-thinking cybersecurity approach.
ZTA's proactive principles, emphasizing continuous verification and least privilege access, empower Hardshell to challenge traditional security paradigms. This user-centric approach ensures rigorous authentication for every user and device, minimizing attack surfaces and swiftly detecting and responding to anomalies.
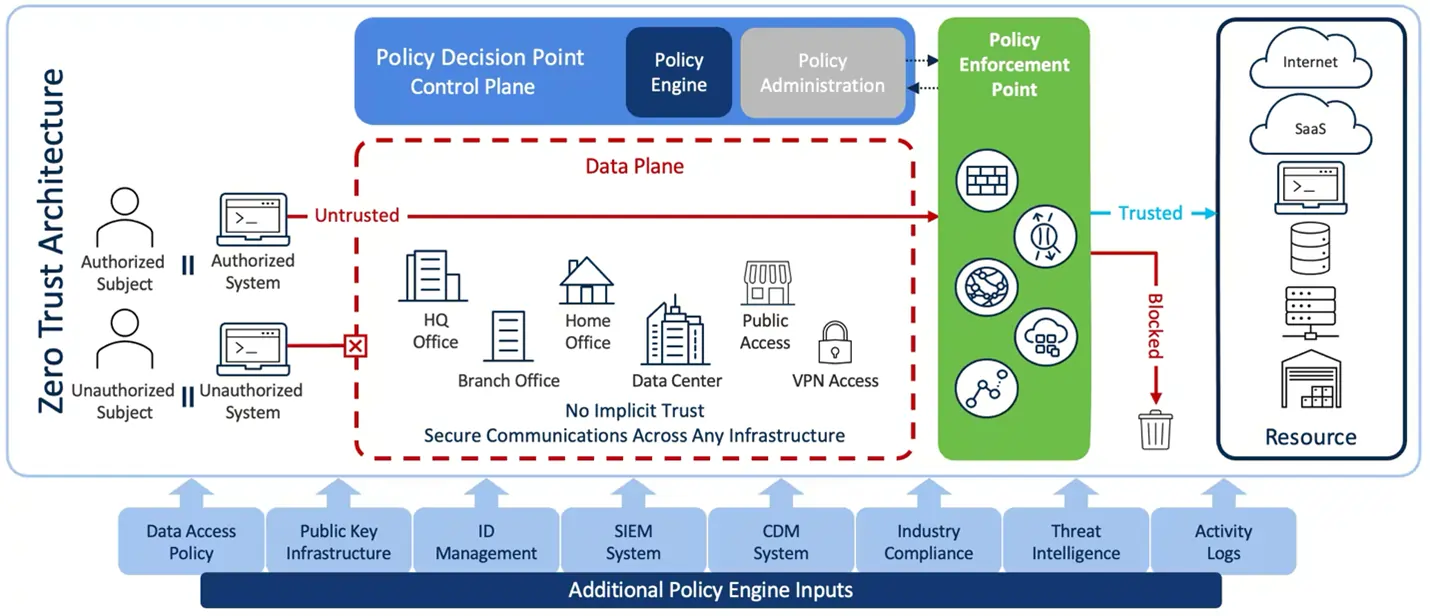
ZTA HIGHLIGHTS
- Focus: ZTA focuses on the concept of "never trust, always verify." It challenges the traditional security model that assumes trust within the network and advocates for continuous verification of users and devices, regardless of their location or network connection.
- Trust Assumptions: ZTA assumes that no entity, whether inside or outside the network, should be trusted by default. Every user, device, and application must continuously authenticate and verify their identity before accessing resources.
- Principles: ZTA principles include least privilege access, micro-segmentation, continuous monitoring, and the idea of treating every network request as potentially malicious until verified.
- Implementation: ZTA involves the implementation of technologies such as identity and access management (IAM), multi-factor authentication (MFA), micro-segmentation, and continuous monitoring. It's more specific in terms of adopting a specific security model.
- Adoption: ZTA is a specific cybersecurity model that organizations may choose to adopt as a paradigm shift in their security strategy. It's often associated with modern approaches to cybersecurity.
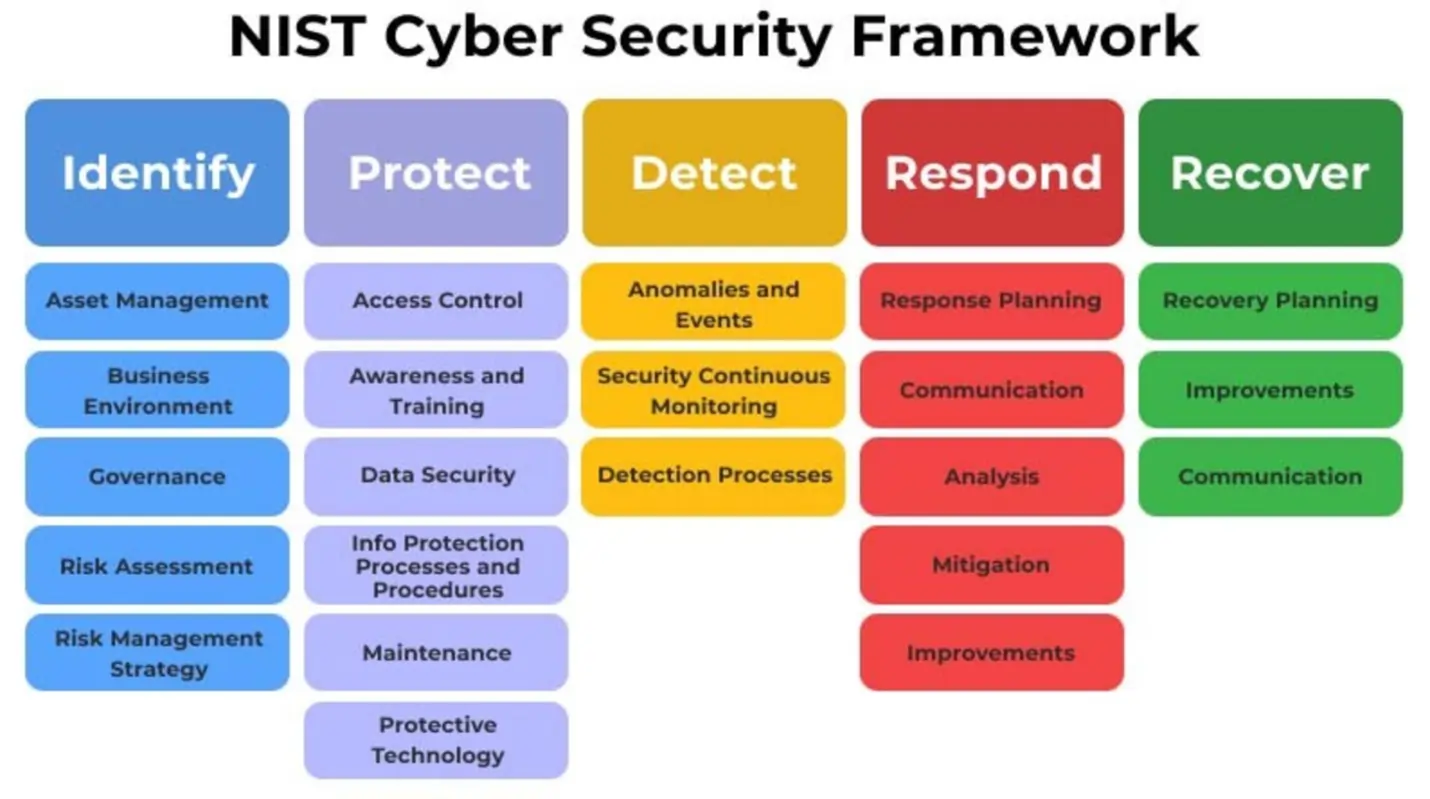
National Institute of Standards and Technology (NIST) Framework
Simultaneously, the integration of the NIST Framework provides Hardshell with a robust foundation for comprehensive risk management. Aligned with the NIST functions, the company effectively identifies and prioritizes assets, implements protective measures, and responds to incidents promptly.
This dual strategy, combining ZTA's dynamism and NIST's proven methodologies, positions Hardshell to navigate the ever-evolving cybersecurity landscape landscape with resilience and adherence to industry best practices and regulatory standards.
NIST HIGHLIGHTS
- Focus: The NIST Framework emphasizes a holistic approach to cybersecurity risk management. It provides guidelines and best practices for identifying, protecting, detecting, responding to, and recovering from cybersecurity incidents. It is broader in scope and not explicitly focused on the zero-trust paradigm.
- Trust Assumptions: While the NIST Framework doesn't explicitly adopt the "zero trust" terminology, it emphasizes the importance of continuous monitoring, risk assessment, and adaptation to changing threats. It does not assume trust without verification
- Principles: The NIST Framework is built around five functions: Identify, Protect, Detect, Respond, and Recover. It encourages a risk-based approach, continuous improvement, and a comprehensive view of cybersecurity.
- Implementation: The NIST Framework is more flexible, allowing organizations to implement a wide range of cybersecurity measures based on their risk profile and needs. It provides guidance rather than specific implementation requirements.
- Adoption: The NIST Framework is widely adopted across various industries and sectors. It is often used as a foundation for building and improving an organization's overall cybersecurity program.
CYBERSECURITY FEATURES
• Vulnerability Assessment: Identify and evaluate potential vulnerabilities.
• Penetration Testing: Simulate real-world cyber attacks to discover and remediate vulnerabilities.
• Prepare for and respond to security incidents, minimizing damage and ensuring a quick recovery.
• Develop and implement an incident response plan with communication protocols.
• Collect and analyze security event data for real-time monitoring.
• Utilize SIEM tools to identify potential threats.
• Implement and manage firewalls to control network traffic.
• Deploy Intrusion Detection and Prevention Systems (IDPS) for threat identification and prevention.
• Protect individual devices from security threats.
• Use antivirus software, endpoint detection and response (EDR), and encryption.
• Control and manage user access to systems and data.
• Implement strong authentication mechanisms, including multi-factor authentication (MFA).
• Encrypt sensitive data during transmission and storage.
• Apply encryption protocols for communication channels and databases.
• Educate employees and users on cybersecurity best practices.
• Raise awareness about social engineering threats and phishing attacks.
• Identify, assess, and mitigate potential risks to information assets.
• Continuously monitor and reassess risks in response to the evolving threat landscape.
• Identify, assess, and mitigate potential risks to information assets.
• Continuously monitor and reassess risks in response to the evolving threat landscape.
• Regularly update and patch software and systems to address vulnerabilities.
• Establish a patch management process for timely application of security updates.
• Implement monitoring tools to detect unusual activities and security events.
• Maintain logs for auditing and forensic analysis.
• Conduct periodic security audits and assessments.
• Ensure compliance with industry regulations and internal security policies.
• Implement regular data backups to prevent data loss.
• Develop and test a comprehensive disaster recovery plan.
• Establish and enforce secure configuration settings for hardware, software, and network devices.
• Regularly review and update configurations based on security best practices.
• Outsource aspects of cybersecurity management, including monitoring, incident response, and maintenance.
• Leverage external expertise for a comprehensive cybersecurity strategy.
• Ensure the security of data and applications hosted in cloud environments.
• Implement encryption, access controls, and compliance monitoring for cloud-based assets.
• Collect, analyze, and share information about current and emerging cyber threats.
• Enhance security posture with up-to-date threat intelligence.
• Provide expert guidance on cybersecurity strategy, risk management, and compliance.
• Assist organizations in building a robust cybersecurity framework.
• Offer training programs and certifications for individuals seeking expertise in cybersecurity.
• Develop a skilled workforce to address cybersecurity challenges effectively.
















